Hack The Box: Mailing
What will you learn? Mailing is an easy rated Windows machine that runs a mail server and hosts a website vulnerable to directory traversal. This can be exploited to allow access to the mail service configuration file, revealing an Administrator password hash. Cracking this hash reveals the password for the Administrator account. Leveraging CVE-2024-21413 in the mail application on the remote host allows for the capture of an NTLM hash for a user on the target machine. Cracking this user’s NTLMv2 hash allows attackers to use WinRM to access the machine. The privilege escalation features a CVE For Libre Office: CVE-2023-2255.
Let’s begin enumerating the box:
The following ports of interest are open: 25 (and the other mail supporting ports- 110, 143, 465, 587, 993, etc), 80, 135, 445, and 5985. There is a lot of good stuff here potentially to begin enumerating.
We can attempt to visit the webpage, it will redirect to mailing.htb. So we can add that to our hosts file with: echo "10.10.11.14 mailing.htb" >> /etc/hosts and refresh. Using Wappalyzer shows us PHP is running on the backend along with Microsoft IIS and the target is a Windows Server OS. The mail server running is powered by ‘hMailServer’. So we can begin learning about that service (deployment guides for credentials, configuration files, etc).
The bottom of this page also has a download instructions PDF file, 16 pages long. This may have some good stuff in it. There is a mention in this document about the person using “user:password” as credentials at one point, and a reference to “after all this ‘maya’ should see our mail” so we have a username. If we use exiftool against the PDF file we can view the meta-data to look for additional information potentially.
There is nothing else useful to us. It is worthwhile to also check the link to the website about hmailserver as well. There are many deployment guides. Looking up default credentials for this we learn the username is Administrator typically and the password is set during the installation. We’re also able to get the location of the configuration file which may come in handy later.
I started to enumerate the web application looking with the development tools (seeing where requests go, storage of cookies potentially, and source code), looking for subdomains (no yield), alternative subdirectory webpages (only found /assets and /instructions). I did not see any input fields where I could test for Cross-Site Scripting (XSS) or SSTI (no templates detected easily in the backend either).
I don’t know the version of this application yet. I tried looking around for that, no luck, but I found some exploits available between local exploitDB and the wider internet.
Visiting the Exploit-DB ‘PHPWebAdmin’ file inclusion page is good. in theory. We could enumerate with some of the payloads mentioned and attempt to find that configuration file we were looking for earlier.
We can open Burpsuite and attempt to manipulate where /download.php?file= and target these files or the one we found by suggestion of Google earlier.
Attempting to reach the hosts file is a success. Taking that GET request and sending it to repeater allows us to test and see what happens. Now we can attempt to find the configuration file itself. We have an idea of the path, but over researching online I found that a potential path is either c:\program files (x86\hMailServer\Bin\hMailServer.ini. or the same in program files.
We are able to get this file with credentials we can attempt to decrypt. By URL encoding the payload, replacing / with %2f and spaces with + we are able to reach it.
I was trying to crack this with Hashcat and it was not working. Using John will work though, using the same wordlist of rockyou.txt. This reveals a password that we can attempt against the maya user account. The other hash we found there did not yield a result.
We have a mail server running on the target, so we can actually connect to this using netcat or use a tool called swaks to check if we can authenticate to a mail server a lot easier. When we run this against the target we do see we’ve authenticated.
We remember the instructions mentioned ‘Windows Mail’ or Outlook, so we can search for a Windows Mail Exploit on Google and find a lead. Another option would be to phish by sending emails for users, but that is not in this box. We can download the exploit to use to our machine with git clone https://github.com/xaitax/CVE-2024-21413-Microsoft-Outlook-Remote-Code-Execution-Vulnerability.git
We are configuring the payload to target port 587, using our credential paring at the domain address we know. Then specifying maya@mailing.htb as the recipient since that’s the only user mentioned. Then for the URL we will specify an UNC path to our impacket-smbserver which we will start prior to executing this payload below.
When we execute the payload we will get a callback from the target machine to our SMBSERVER sharing the current working directory, as an smbshare named smbFolder.
We received a NetNTLMv2 hash (hashcat mode 5600), which we can crack now and see if we get a clear-text password from it.
Now we can use this password to get a session on the machine with the user maya with EVIL-WINRM to take advantage of the open win-rm port.
Then we’re able to get the initial access and user.txt flag.
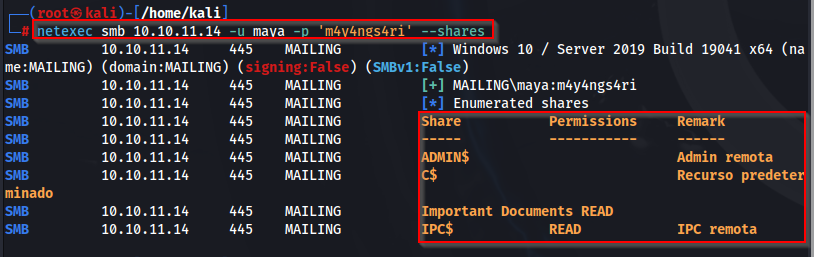
We can also use netexec (crackmapexec) in order to look for any shares this user may have access to, and we see that it does. So we can enumerate the file system for these shares and see what exists there.
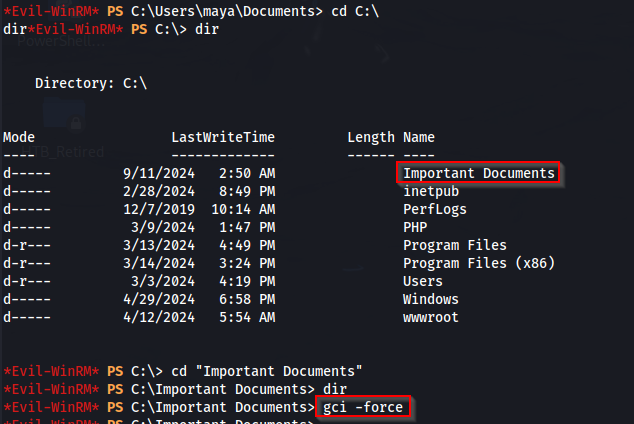
When we go there we do not see anything, and we can use gci -force to find potentially hidden files as well. Which there are none.
If we look into the Program Files directory we can see some interesting things like GIT and LibreOffice (which is more unusual on a windows machine).
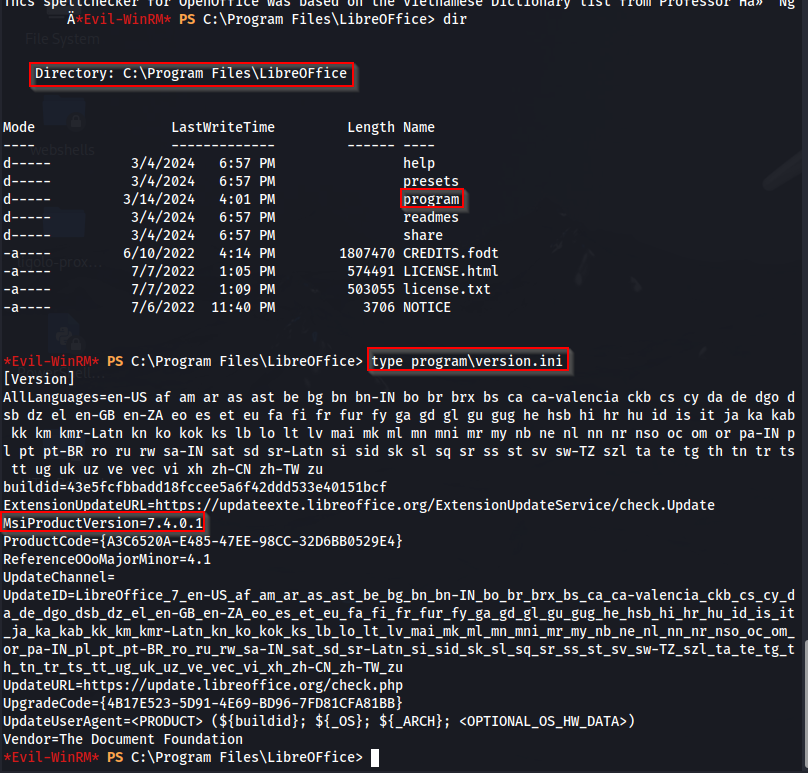
We can enumerate the version of this program through the program directory, that has a version.ini file revealing version 7.4.0.1.
If we search for exploits for Libre Office 7.4.21 we can find a potential candidate to use.
We can pull this to our local machine and start creating a payload: git clone https://github.com/elweth-sec/CVE-2023-2255.git. So we can use this exploit to run nc.exe on the target machine to return a shell back to us as a privileged user.
Upload netcat.exe to the target using upload with evil-winrm.
Now we can refer to the instructions on the GitHub repo and create our payload using the Python script and create a method for it to call back to our netcat listener.
Create a netcat listener to run in the background matching our payload.
Then we can place the exploit into the Important Documents directory, which stands as a good chance of being used by the users.
Then the ‘user’ opens our file and it runs the exploit, returning us a shell as the administrator user account. We have successfully rooted mailing!