Hack The Box: Forest
What will you learn? Forest is an easy rated Windows machine configured as a domain controller where an exchange server is installed. The DC allows for anonymous LDAP enumeration which leads to an initial foothold through an insecure service account. This service account is in an overly permissive group that allows for users to be added to the exchange group. This groups allows for a Dcsync attack on the domain controller, which allows for credential dumping from the AD database to obtain all the NTLM hashes of users in the domain.
Let’s start enumerating the box:
The following interesting ports are open on the target: 135 (rpc), 389 (ldap), 445 (smb), and 5985 (winrm).
We’re unable to enumerate SMB without a user account:
Running nmap enumeration scripts we’re able to find a ton of information about the domain, sensitive information too. nmap -sV --script "ldap* and not brute" 10.10.10.161. This will deliver a ton of information so it may be wise to pipe it into less or direct the output into a text file for analysis.
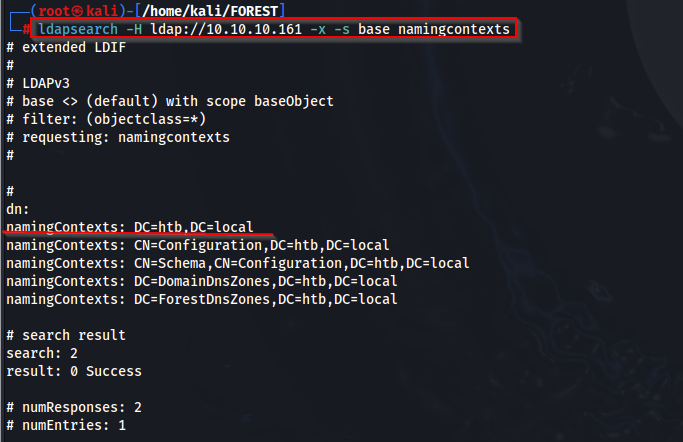
Next we can check for the specific naming context and find it is DC=htb,DC=local”
We can cut out all the user accounts using grep and specifying the samaccountname text and output it to a file. Then chop away the extra bits we don’t need.
Chopping away the other parts prior to the colon we can create a real user list. Now we just need to find passwords exposed in this anonymous LDAP bind listing or create a list of predictable passwords based on context we acquire.
We can chop out all of the unnecessary stuff from the domain, Microsoft exchange, and machine accounts indicated by a $ and this leaves us with a list of 5 user accounts.
Now we can create a password list. This can be done with a good sense of what to do with adding all of the months of the year, seasons, some relevant words, very general words like password and so on.
This saves time compared to rockyou.txt sometimes as user’s do these things. Then we can add to the passwords in our list using bash for loops to state the original, append 2019 to it, and 2020 on separate lines which gives us a lot more to work with. I watch a lot of IPPSEC videos and highlighting some of the things I learn from him are really helpful to reference later and for readers (note).
Moving on, when using enum4linx-ng to enumerate for similar information- this actually reveals a username to us that we previously did not see. Illustrating the need to check with more than one type of tool: enum4linux-ng -A 10.10.10.161. This is a service account given the naming convention too.
We do not have any real credentials that were usable to this point. Next, especially in lieu of seeing a service account, we can attempt asreproasting: For user accounts that are enabled with no Kerberos pre-authentication they are vulnerable to ASREP Roasting attacks. This allows attackers to request the Kerberos TGT without requiring a password. This will send us back a hash for the user account that we can crack and this is achievable using the impacket tool GetNPUsers.py
Now we can crack the hash we just obtained using the mode 18200 and we’re able to obtain a cleartext password of s3rvice.
We can test authentication with netexec (crackmapexec) and attempt to login with windows remote management (evil-winrm) successfully after the verification.
Now we need to enumerate our groups, privileges, other users, and get a sense of what we’re dealing with on the target:
We can see there are a fair amount of users on this domain.
Our account does not have anything too interesting, besides being a service account group member.
This is not showing any immediate wins.
At this point we should both transfer winpeas for automatic enumeration to the target and bloodhound to get an idea of the connections in the domains, where privielge’s may be able to be abused. Manual enumeration through Powerview is also a good alternative here.
We need to start both the neo4j console (service) and bloodhound, premeptively.
Now we need to transfer and run Sharphound on the target to create a zip file to exfiltrate back to our attacker machine, for importing into Bloodhound to analyze.
Then we can upload a Windows MSVC server to the target to help our exfiltration effort (no need for netcat or alternatives) and we can request our zip file directly from the target after hosting it: https://github.com/TheWaWaR/simple-http-server/releases?source=post_page-----66baa18b6460--------------------------------
After requesting it we now have the zip file to drag into BloodHound’s main UI and see what is going on in the domain.
It will take a while to load the data into bloodhound. After it loads, we can start looking.
Right click on SVC-ALFRESCO on the middle of the screen, and mark user as owned. Then click the top left under queries, and select ‘Shortest Path from Owned Principles’. We will get the result below.
SVC-Alfresco is a member of service accounts which is as member of privileged IT accounts, which is also a member of account operators. The account operators group has a ‘GenericAll’ permission set on the exchange windows permissions group which has WriteDacl permissions on the domain.
We are going to create a user on the domain which is possible due to the account operators group membership.
Add this user to the exchange windows permissions group which is possible due to the generic all permission set.
Then give the user ‘DcSync’ privileges which will allow us to dump all the credentials in the domain when we follow through and perform a dcsync attack.
Then perform a pass-the-hash attack or use the cracked credentials to access the local administrator user on the domain.
Starting with creating our user account:
Adding our user to the Exchange Windows Permissions group
Giving the user DCSYNC privileges (this will require powerview.ps1) with the following payload from 0xdf:
Add-DomainGroupMember -Identity 'Exchange Windows Permissions' -Members cyberwired; $username = "htb\cyberwired"
$password = "password"; $secstr = New-Object -TypeName System.Security.SecureString; $password.ToCharArray() | ForEach-Object {$secstr.AppendChar($_)}
$cred = new-object -typename System.Management.Automation.PSCredential -argumentlist $username, $secstr
Add-DomainObjectAcl -Credential $Cred -PrincipalIdentity 'cyberwired' -TargetIdentity 'HTB.LOCAL\Domain Admins' -Rights DCSync
Now we can perform the DCSYNC attack with our new user account and continue.
I tried cracking at least the administrator user hash, to no avail, as planned went with the pass-the-hash attack using impacket’s psexec.py and obtained access the NT AUTHORITY\SYSTEM user and obtained the root.txt file