Hack The Box: Bashed
This is a really simple Linux box. A great start for CTFs.
Initial Enumeration
This is a HTTP-only scenario.
We’re able to find a number of directory listings, potentially able to find information in these.
Directory listing response from Gobuster to enumerate potential web directories. Once we have a good idea of what is out there on this webserver, we can start visiting to learn more.
When you find potentially interesting files and folders, you should dive deeper.
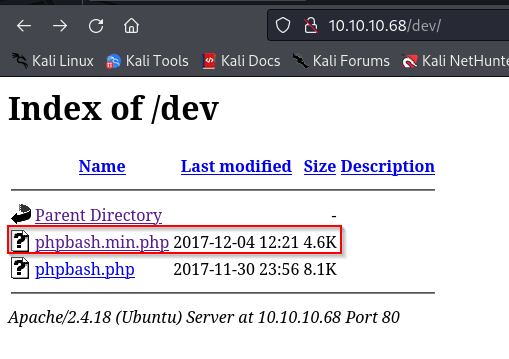
The /dev page has a PHP webshell at phpbash.min.php where we’re able to interact with a Linux target remote host. PHPBASH is a common webshell that is positively interactive for penetration testers, a good tool in the arsenal: https://github.com/Arrexel/phpbash
Reading files like /etc/passwd is great to get an idea of who is available, has shell access, among other things.
Running sudo -l to find that we can run with super user privileges with scriptmanager.
If we remember from our /etc/passwd output above there is a user account named scriptmanager. We can probably run commands with SUDO as the script manager user. First we should create a reverse shell. Start a listener with netcat.
Start a netcat listener.
Create a busybox netcat reverse shell from https://www.revshells.com/
We’re able to see we have a reverse shell as the www-data user.
Checking to see what version of Python gives us options. We can spawn a interactive shell session with Python to make a better shell. Use this source for many options to spawn interactive shells: https://0xffsec.com/handbook/shells/full-tty/
We are now the scriptmanager user.
Now that we are the scriptmanager user. We can enumerate what privileges this user has, repeating the sudo -l method.
This is a dead end.
We are unable to retrieve the sudo entries for this user. We are going to have to go back to manual enumeration efforts. Alternatives are using tools like linenum, linpeas, etc. To streamline the process. We will check the users home directory.
In this case the only thing that stands out is in the top level directory / where there is a non-standard scripts folder. Always look around for non-standard folders.
Two potentially interesting files.
We do not have permissions to edit these files.
There is a Python script to write output to test.txt.
We are able to see the creation time of test.txt. If we pay attention by running ls -la or equivalent often we can see that it is being recreated over and over. This makes a reasonable assumption that a cronjob is running that python file to output to test.txt and it is outputting as the root user. So if we can replace the python file contents with a reverse shell then we should be able to escalate to the root user.
Start a netcat listener on a port 3333.
The payload.
Create a python reverse shell file named test.py from https://www.revshells.com/. Make sure to use Python payload #2, you will have to extrapolate it into a more “feedable” way for this scenario to work.
Host your file on a python3 web server.
Copy your new test.py.1 to the old name so it runs via the cronjob.
You will get a reverse shell connection as the root user.
Congratulations, you’re the root user. This box can be very finnicky but is a great opportunity to get familiar with using sudo under different user contexts, introducing cronjobs for privilege's escalation, looking for non-standard directories for “juicy” information or files, and more. I hope you enjoyed ‘BASHED’.