PowerShell Empire for Red Team Operations
What is PowerShell Empire? This is one of the many C2 (Command and Control) frameworks that exist that an open-source post-exploitation framework. A rival of Cobalt Strike (a popular commercially available C2 tool). It is used in Red Team Operations and penetration tests, uniquely implementing the capability for running PowerShell agents that do not require powershell.exe. Containing many modules including keyloggers, Mimikatz, and other means to evade detection.
It is very similar in aesthetic and usage to the Metasploit Framework. PowerShell Empire is no longer maintained by the original authors. but is currently used and maintained by BC Security, see: https://github.com/BC-SECURITY/Empire
Definitions:
C2 - Command and Control
Server - Technical infrastructure and protocols that allow threat actors to manage and coordinate malicious activity.
Agent - Allows you to maintain a connection to a target by providing information about a target.
Stagers - These connect to the Empire server. They then create an agent which you can interact with and use to control compromised systems (they run modules), facilitates the running of malicious code.
Listener - Service running on the attacker C2 server that is awaiting a callback. This allows stagers to connect to the server.
Modules - These are pre-configured ‘exploits’ or ‘payloads’ for you to attach to your configured stager/listener, for example, a keylogger module.
Starting the PowerShell-Empire client/server model:
In order to start the PowerShell Empire client you first must start the server. This can be done by doing sudo powershell-empire server. You will get a bunch of feedback of the starting of the Empire server.
Once you have started the server you’re now able to start the client where it will now interface with your server with the following: sudo powershell-empire client.
Introducing the Empire Web Application GUI (Starkiller):
Starkiller is a web application that serves as the front-end for PowerShell Empire. This provides ethical hackers a graphical user interface (GUI) to interact with agents, manage modules, and inspect data. It comes pre-packaged with Empire 5.0 and later. It hosted here on GitHub: https://github.com/BC-SECURITY/Starkiller.
We are able to interact with the user-friendly interface by visiting the link that our server spins up. This will greet us with a login page where we can authenticate with the default credentials of empireadmin and password123. These can be changed at your discretion.
This is your workspace where you will be able to see your listeners, check or uncheck modules in-use, see all your agents, and interact with them in a user-friendly way. We do not need to use this however as we can do what we need from the client itself too. It is important to notate you have these options and they’re incredibly valuable at scale.
Introducing Listeners in PowerShell Empire:
The first thing to look at when using any tool is the help menu which can be accessed by sending help in your client:
The first one we will use is the LISTENERS capability. When we run this command it will show we have no active listeners and it will show that we have selected the listeners command set. To exit out of this option or any others we can just type back. In order to select the type of listener we want to use we can provide uselistener http for HTTP or provide another type.
We are able to see the options of the listener we are setting up by sending the options command. This provides context about details like the binding IP and port (networking information that must match payloads sent to targets), kill date (date for the listener to exit), name for the listener (to better manage agent connections), and we can configure these ‘Metasploit like’ options a lot more granularly. The syntax to change one of these is set <option> <value>.
To start a listener we can type the command execute and it will be listening for connections.
We can call the commands listeners in order to see a list of what we have enabled or created so far too.
Selecting a Stager and Beginning to Think Like an Adversary:
We have many stagers available to us in the format of automatic suggestions you will notice as you type. One that is particularly interesting to play with in labs is a Windows BAT file launcher. The description mentions a valuable point for red teamers too, the payload is a self-deleting .bat launcher and it even mentions only HTTP and HTTP COM listeners are compatible.
A self-deleting payload means there are less left-over Indicators of Compromise (IoC), or artifacts, left over by the offensive security team that could lead to being discovered by a blue team or users - which leads to detection, deletion, and potentially the end of your access as an adversary.
We can now configure the options of the stager and attach our listener, then set other options like adding obfuscation (to evade detection, make the PowerShell code unintelligible).
Transferring the Payload to the Target Machine in Order to Obtain an Agent:
The listener and stager are created and you can reach it where it says it is written. You can transfer the binary created to the target using LOLBAS suggestions for native CMD or PowerShell commands like either certutil, iwr, or other means of transporting files to a Windows target (due to the BAT file). Living Off The Land Binaries is useful context for understanding what is in the environment already to be taken advantage of for your offensive purposes.
On the target machine you can run the payload that has been created (this will tell you a new agent has been checked in).
Due to the generation of the names that may not be friendly to us in managing a C2 framework, we can change the name of the agent (target) we received. This can be done using the command rename <name> <newname>. We are also able to list the agents we have running using the command agents which is fantastic for viewing what we have access to.
We can now interact with our agent which means we can spawn an interactive command line session. We are able to send commands. Something to keep in mind is commands that are run will be logged somewhere and EDR, A/V, SIEMs, or other security monitoring software may search for certain phrases and blue teams who are doing their job correctly will be aware of commands being sent too.
Privilege Escalation Modules in PowerShell Empire:
PowerShell Empire has hundreds of modules written in different languages for use. There are many modules that are created to obtain privilege escalation from a regular user to a local administrator as well. Similar to the Metasploit capability to escalate to the ‘root’ user or ‘NT AUTHORITY /SYSTEM’ user automatically using whatever the shortest path first is, we can do that here too by doing getsystem.
Elevated (targets that we have administrator access on) agents will have a * next to their name when we send the agents command to list them out.
Create an elevated command prompt on a Windows lab machine which runs as NT AUTHORITY /SYSTEM, and run launcher.bat, it will check in a new agent for us.
To use the privilege escalation module to automatically elevate privileges: usemodule powershell_privesc_getsystem
After selecting that module we can select the agent (set agent <name>) and execute it to obtain access as an admin.
Creating Persistent Sessions on a Target:
It is at this point where you’re able to add persistence to a target, post-compromise. There are many modules for this which may or may not have good operational security concerns (maintaining cover under the nose of an active security team). Penetration Testers are loud but Red Teamers require long-term access through ‘stealthy’ actions to emulate the behaviors of Advanced Persistent Threats (APTs).
Our goal is to maintain access after reboots or disconnections, a low/slow approach where refreshing and interacting will not get our team caught. Notice below we’re able to granularly control parameters such as a schedule. The options reveal a lot more that helps us ‘hide in plain sight’ check them out and think with an attacker mindset.
We can use the powershellpersistence_elevated_schtasks module to achieve this for example.
Post-Exploitation Modules in PowerShell Empire:
There are more than just privilege escalation modules available to us. We can use post-exploitation focused modules on dumping NTLM hashes, clear text credentials stored on the target, steal kerberos tokens, tickets, and modules to perform lateral movement in a domain or among joined systems in any network.
To dump the credentials on the machine (acquire NTLM hashes) we can use the module usemodule powershell_credentials_invoke_ntlmextract
This will perform a similar function to the tool Mimikatz. These hashes can be cracked to reveal cleartext passwords using tools like Hydra, John The Ripper, or online on a service such as https://crackstation.net/ or be used with crackmapexec (or netexec, or many other tools) to test for access by performing Pass-The-Hash (PtH) attacks.
For proof of concept of what we can do with these hashes now. I will crack the CyberWired user hash with Hashcat, connect to the machine another way without cracking the password, and show how you can test against machines for access.
To show an example of password re-use: I enabled the default Administrator user account and set the password to the same as the CyberWired user.
Cracking the user account password with hashcat using Rockyou.txt to find a very weak password. See below as we can use that password against another user account (in this case the administrator) to authenticate and acquire a shell on the target as an Administrator.
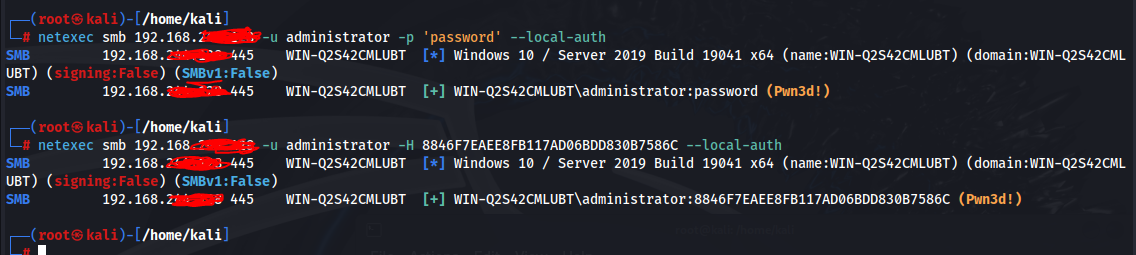
We can also test remotely using crackmapexec (or its updated version: netexec) and see if a password we have works against a user, or if the hash we acquired works against the user account. Seeing Pwn3d! means we have access as an administrator user. Another cool thing to note, we can change the protocol from SMB to SSH, RDP, WINRM, etc to see if we have other means of accessing the machine.
Thank you for reading, I hope this shows exactly how useful PowerShell Empire could be in capable hands and demonstrates a practical scenario and steps that may be taken in an actual red team engagement.